This post explores insights and trends gathered from data that Anvil Secure collected while delivering projects to a wide range of clients.
The Types of Issues We Analyzed
The statistical data reflects the years 2022, 2023 and 2024. We grouped all the issues into a set of high-level categories and focused on the six categories containing the most issues:
- Access Control: issues related to allowing authentication and access to resources to only the users permitted to use them
- Communication: issues surrounding the usage of TLS or encryption, including the latest guidance on preferred algorithms and ciphers
- Configuration: issues that relate to hardened build and production environments
- Data Protection: issues focused on maintaining confidentiality, integrity, and availability
- Error Handling: issues related to logging errors and making them useful for users as well as administrators and incident response engineers
- Validation: issues related to validating all data that crosses a trust boundary
While other categories (Architecture, Business Logic, Malicious Code, etc.) have their place and are informative, we chose to focus on these six categories as they have encompassed 90% of the found issues for the past three years.
5 Key Trends
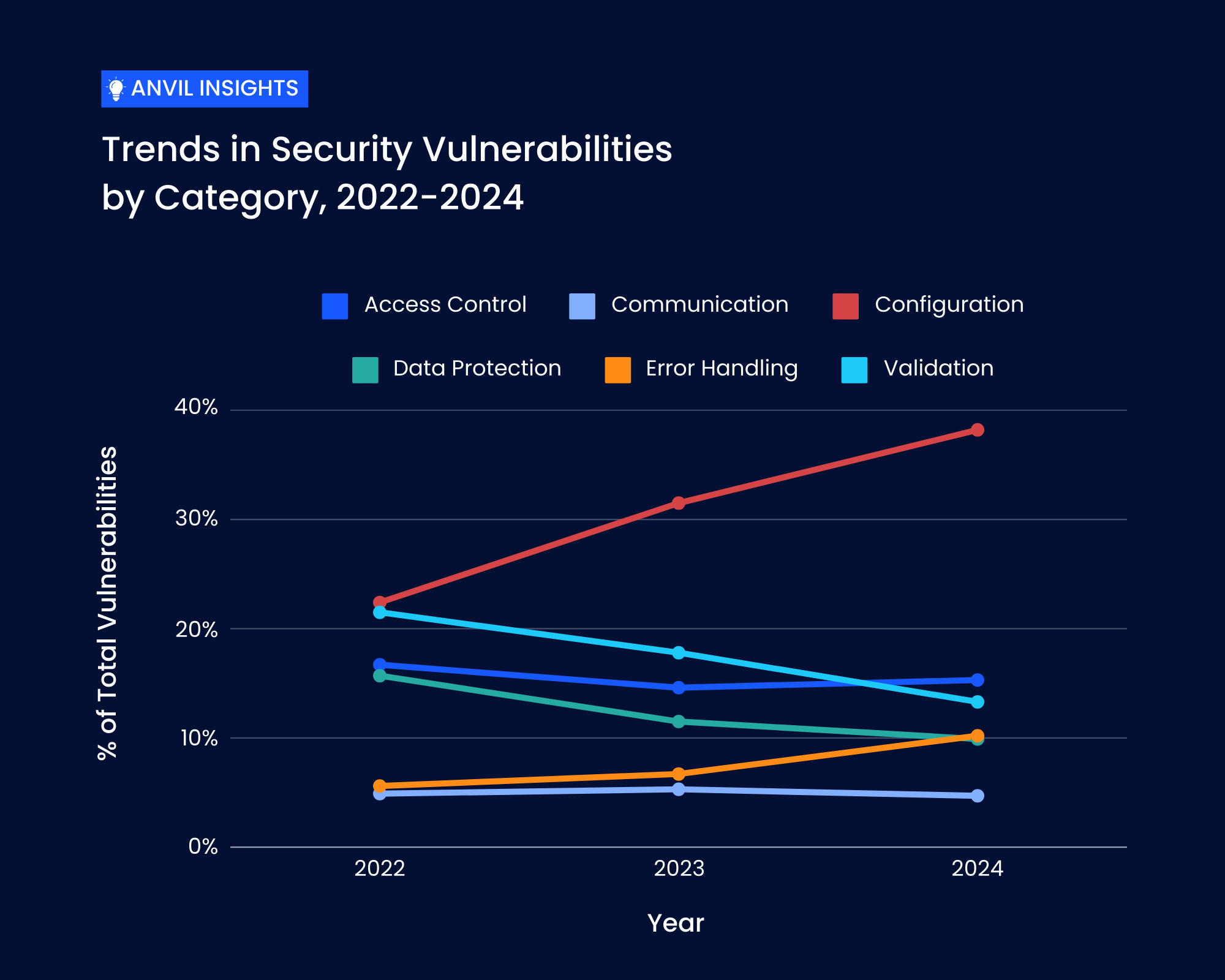
1. Access and Communication Issues are Consistent but Stable
Access Control issues account for roughly 12% (1 in 8) of our findings each year and remain rather stable. This category would include authentication as well as authorization and access control-type issues. Similarly, the Communication category accounts for approximately 5% (1 in 20) of the total issues found. Issues in this category often relate to (the lack of) TLS usage or its configuration.
2. We’ve Seen a Significant Decline in Data Protection Issues
In the past three years we also saw a precipitous drop in issues surrounding Data Protection from over 1 in 8 to less than 1 in 10 issues. This suggests that for our long-standing clients, their partnership with Anvil is paying off as there have been fewer issues related to protection of data. Regardless of whether this is indicative of better client practices, such as storing data protected properly with encryption or key management, this trend suggests that our clients improved tremendously in this area.
3. Fewer Validation Issues Indicate Stronger Safeguards
We saw another drop in issues surrounding Validation. Our clients improved in the sanitation and validation of untrusted user input, as well as the performance of appropriate output encodings. Over the last three years, Anvil saw this type of issue drop by over 22%, (from 1 in 5 to just about roughly 1 in 8 issues).
4. Error Handling Issues are on the Rise
Conversely, the Error Handling category doubled from around 5% to approximately 10% of the issues filed. This category includes anything related to logging and alerting, which is very important in modern software-as-a-service infrastructure.
5. Configuration Issues are Rising Faster than Any Other Category
The Configuration category also jumped from just shy of 25% to nearly 40% of all the issues identified over two years.
Severity of Issues
By contrast, the severity of the issues does not expose much of a trend. Notably, the more mature the security posture of the software or hardware we analyze, the lower we find the overall severity of the issues. Of course, this does not consider black-swan events, and a critical severity issue can always pop up at a later stage.
Overall, one thing that does remain consistently reliable is the number of issues with a “High” severity rating. Regardless of the project scope, duration, the year of engagement, the engineering team, the client's security maturity, or the organization's size, we see that around 15% (roughly 1 in 8 findings) will have a “High” severity rating assigned to it. However, this number is an average for all the projects analyzed in this period, and this trend does not account for projects where we find many more vulnerabilities with “High” or “Critical” severity ratings. It is also less representative of projects where a more mature security posture exists, as those vulnerabilities will be more often scored with “Medium” or “Low” severity ratings.
Takeaways
Given Anvil’s limited dataset, the more specific trends we found may not necessarily reflect those of the wider information security community. Nevertheless, based on our experience and recent industry news, we note the following general themes:
- A shift to declarative infrastructure via Infrastructure as Code [3] over all our clients. This leads to an increase in issues related to Configuration as well as Error Handling. This makes sense as shifting to modern cloud practices will lead to more issues in these declarations as well as how and what to log.
- Data Protection is being handled better. Improvement of tooling, knowledge and out-of-the-box available key management solutions as well as modern libraries and even compliance efforts help with reducing TLS and related issues.
- Validation has tremendously improved. This is a combination of, first, appropriate data validation via frameworks, formal data models, modern languages such as Go and Rust and modern communication frameworks such as gRPC. We can also measure the improvements our clients have made over the specific time frames mentioned by adding extra automatic tooling in their CI/CD infrastructure or simply disseminating previous reports from us and using that to train their own engineers.
A Word about Methodology and Limitations
Over the last five years, Anvil has developed a custom project management system (Nexus) based on the collective experiences of our employees and their decades of industry practice. Nexus helps us to maintain a high level of quality of work and to collect statistics from findings we have identified and reported to our clients.
The above-mentioned data and trends are conditioned upon several factors, including specific contract terms with these respective clients and the fact that our client base varies in size from “Big Tech” firms to startups, and in industry from software development to device manufacturers (healthcare, ICS/SCADA, hardware security solutions, network devices). The projects we perform for these clients likewise span a large range including architecture reviews, application security assurance (code review or gray/black box tests), network penetration tests, and hardware/firmware penetration testing.
Thus, our statistical analysis must account for variable client makeup and project type, and we have attempted to address these variables manually. For example, for certain clients, we include different report outputs in addition to categorization for identified issues in our reports.
Generally, Anvil defaults to the high-level controls specified in the OWASP Application Security Verification Standard (ASVS) [1]. However, for threat modeling engagements we respond to threat categories as presented in the STRIDE model [2]. Anvil uses the terms “findings” or “issues” rather than “vulnerabilities”. This is simply because an Anvil security engineer might flag something useful that is written up for a client in the report, however it might not necessarily be a vulnerability (e.g. something generally known as an informational issue or finding).
Because most issues are vulnerabilities, they have a severity rating regardless of what scoring system we use for our clients. All scoring systems generally use severity definitions ranging from “Critical”, “High”, “Medium”, “Low”, and “Informational."
Contact Us!
We would be curious to know if our findings reflect the experience of your organization. If you have the ability to share some insights, don’t hesitate to email us directly at info@anvilsecure.com. We have cultivated long-standing partnerships with many of our clients and are proud of the progress we are making together on improving their products and services. If you would like to talk about how we can help you reduce the number of issues or move towards a modern technology stack, please reach out.
References
About the Author
Vincent Berg is our Chief Technology Officer at Anvil Secure. His strong technical background and years of consulting experience drive his belief that technical excellence and professionalism should be at the core of everything we do at Anvil. As CTO, he guides research and technical content, while maintaining a client-focused approach

