By Alex Conti
TL;DR
The problem: SAP publishes a long and time-consuming checklist to securely configure your HANA database instances.
The solution: Anvil Secure is launching the first version of a tool that automates running these checklists and produces actional reports for analysis.
Quick Overview in pictures
A sample run of HANAlyzer is as follows:
$ ./hanalyzer query --host $HANA_HOST --db-username SYSTEM --sid HXE --output-folder hana
The initial screen will look like this:
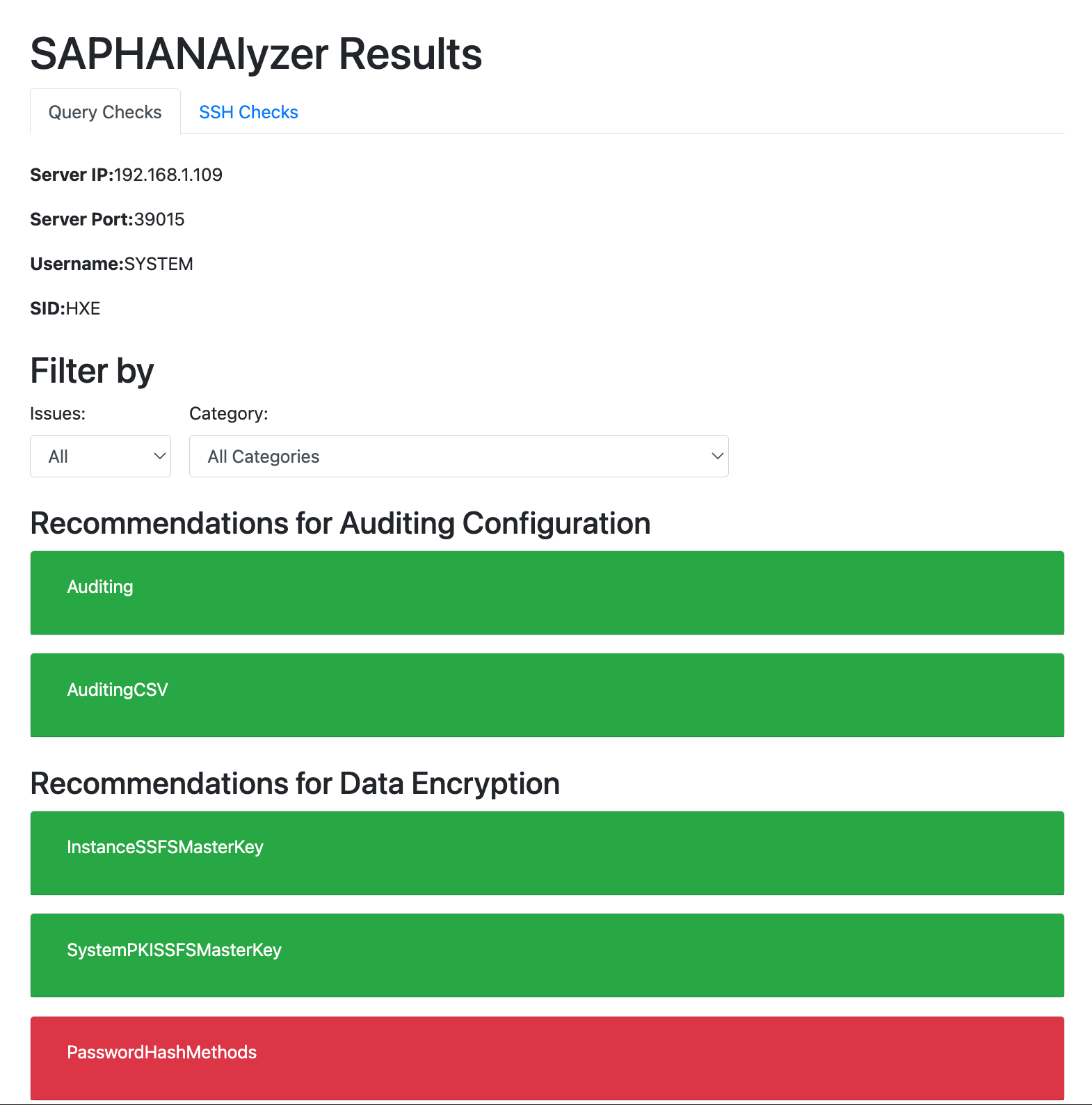
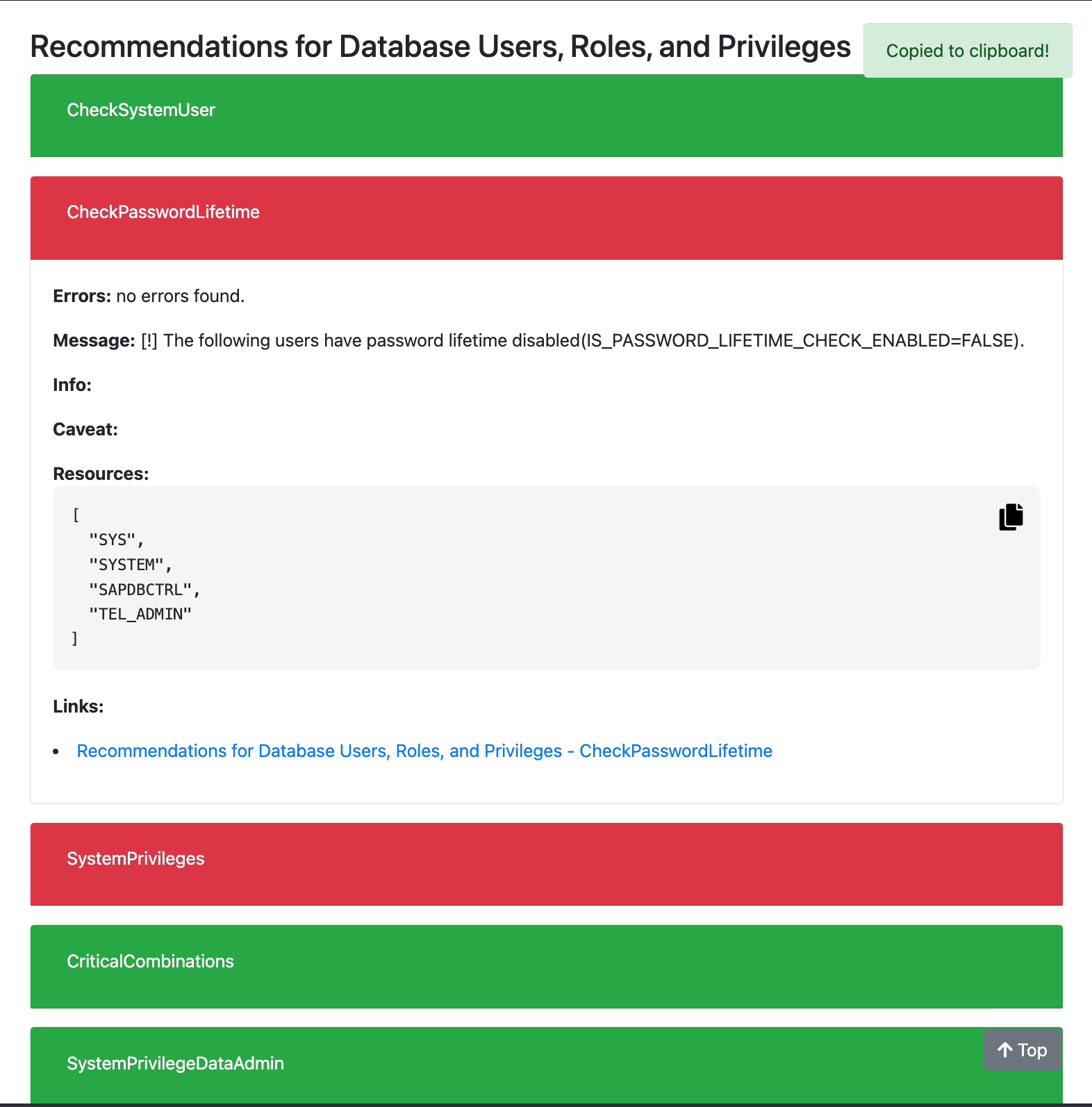
Below is an example of a check result (Password Lifetime of Database Users).
Introduction
As a company, we have had to analyze (more than once) SAP HANA databases and try and find misconfigurations and security issues. SAP provides a checklist (SAP HANA Security Checklists and Recommendations) to help in this process.
It is a thorough list of controls that must be performed.
Since hackers are lazy efficient people, we wanted to automate this process and so we initially created a bunch of scripts to do it.
We are now publishing a tool to automate this process as much as possible, so you can deploy it on a host that can connect to the HANA instance and read the results of the controls by scrolling an HTML report.
Design
What we aimed at:
- Cross-platform compatibility:
We want this tool to run on Mac, Linux, and Windows - Self-contained (executable, no dependencies, no libraries, no internet connection required):
We want to upload it on the machine and launch it, nothing more should be done. - Simple HTML report in output:
We want something simple that can be browsed and read after the scan.
We chose Go to meet all these requirements. It is a compiled language that allows cross-compilation for multiple platforms and architectures. Static files (e.g., HTML templates) can be easily embedded into the final executable itself. Dependencies and libraries can be statically compiled within the binary to make it self-contained, allowing us to ship it directly to the host that will run it.
Where do I find it?
If you have the Go SDK installed on your machine, you can clone the repository (https://github.com/anvilsecure/hanalyzer) and compile it using the makefile.
$ make linux/arm64
If you just want to run it, you can find the latest binary releases on the release page of the repository. Download them from there and simply run the binary!
How to use it
There are two possible modes of analysis:
- Querying the database ("DB")
- Invoking commands via SSH on the DB server (right now it supports the only check we weren't able to run by querying the DB)
If possible, we try to perform checks by querying the DB to avoid requiring SSH access. The only check that was not possible to implement via query is Encryption Key of the SAP HANA Secure User Store.
Passwords (for the DB user or for the SSH user) must be exported to environment variable HANA_DB_PASSWORD / HANA_SSH_PASSWORD to avoid passing it via CLI arguments.
It is also possible to use a configuration file (--conf <file.yml>) or provide the required parameters via CLI flags.
$ hanalyzer -h
Tool to analyze SAP Hana database configuration against official SAP guidelines.
Usage:
hanalyzer [command]
Available Commands:
completion Generate the autocompletion script for the specified shell
help Help about any command
query Perform checks by querying the DB.
ssh Use ssh to perform the following checks on the DB server:
- Encryption Key of the SAP HANA Secure User Store
Flags:
-h, --help help for hanalyzer
Use "hanalyzer [command] --help" for more information about a command.
Configuration file
In the project root, create the following conf.yml file:
host: HOST_NAME
sid: DB_SID
database:
port: PORT
username: USERNAME (e.g., system)
password: PASSWORD
ssh:
port: PORT
username: USERNAME (e.g., hxeadm)
password: PASSWORD
Example
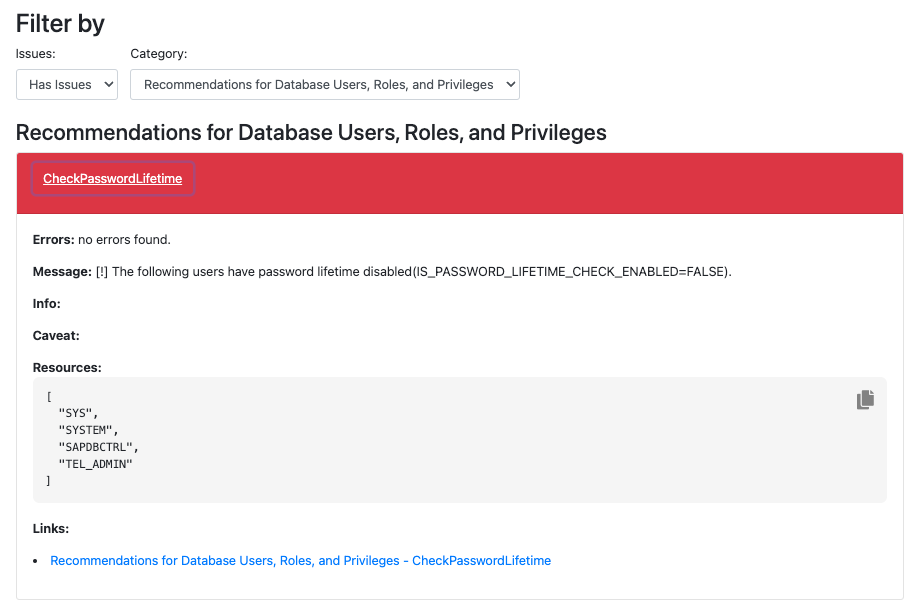
In the following example it will be shown the output of the tool for check Password Lifetime of Database Users.
The recommendation is:
Do not disable the password lifetime check for database users that correspond to real people.
The guideline to verify it is:
In the USERS system view, check the value in the column IS_PASSWORD_LIFETIME_CHECK_ENABLED. If it is FALSE, the password lifetime check is disabled.
The time of the last password change is indicated in the column LAST_PASSWORD_CHANGE_TIME.
The following query will be issued to the HANA DB
SELECT USER_NAME, USER_DEACTIVATED, DEACTIVATION_TIME, LAST_SUCCESSFUL_CONNECT FROM "PUBLIC
In the image below is highlighted the output in the HTML report.
Roadmap
Add sudo support for SSH commands
Improve HTML output
Git actions to automatically compile releases
Conclusions
HANAlyzer is a valuable tool for assessing SAP HANA database configurations against official SAP guidelines with features designed to help identify and address potential security issues in SAP environments. By providing clear documentation on modes of operation, usage instructions, and the ability to configure via a configuration file or command-line flags, HANAlyzer simplifies the process of performing comprehensive security assessments for SAP HANA databases.
About the Author
Alex Conti is a Security Engineer at Anvil Secure with a strong passion for cybersecurity, automation, and offensive security research. He has worked with many different technologies and stacks throughout his career, applying his skills across a variety of environments and client requirements.
His strong drive to automate processes led to the creation of this tool, designed to make it easier for SAP HANA administrators to run checks included in the security guidelines. Automation is one of his many passions, along with chess, philosophy, homelab projects, and the gym.

